Chinese Cyberattacks make hacking a career choice
Hacking in China has become a widespread disease with cybersecurity becoming a popular choice for college graduates looking to trade in their computer skills for quick cash. This can come in many forms such as military led cyberwarfare, civilian hackers targeting infrastructure, hackers deploying ransomware, targeting critical infrastructure, blackmail, and human trafficking to name a few. Another key factor that differentiates Chinese hackers are the lack of any boundaries between intelligence collection and intellectual theft. The huge outcry to ban companies like Huawei and TikTok are sufficient reasons to worry about the lack of data privacy and just how deeply such companies facilitate Chinese hackers into exploiting vulnerabilities.
Latest assessments by foreign intelligence service show that Beijing is using social media in order to influence public opinion and target individuals. Companies like Huawei and Hikvision are being accused of espionage and orchestrating cyber attacks. The recent theft of sensitive company data from Dutch ASML chip provider is suspected of Chinese origin. This is mainly to bypass export control regulations after Xi Jinping widely announced that it would build its own semiconductor and chip-building capabilities. The theft is by no means an isolated incident but a part of regularly organized commercial espionage by China in order to target the economies of other countries.
Mandiant is a US based cybersecurity company that became well known after being at the forefront of accusing China of cyber-espionage in 2013. It is now a Google affiliated company and has carried out extensive work in this regard. A recent report from them showed that China based groups like UC3886 are now beginning to target government websites and large companies in a more sophisticated manner. Instead of directly attacking the company, they are trying to exploit vulnerabilities in software like firewalls themselves. The reason for concern is now is that cybersecurity firms themselves are admitting that the obscure attacks and sophisticated technical capabilities imply that Chinese have far greater access to the network than is previously thought possible. Moreover, discovering the depth of the intrusion is likely to take several years in which time China is fully capable of innovating. The latest attack on Fortinet comes in the wake of the National Security Agency warning companies like Citrix and VMware that they were being targeted by China affiliated hacking group APT5.
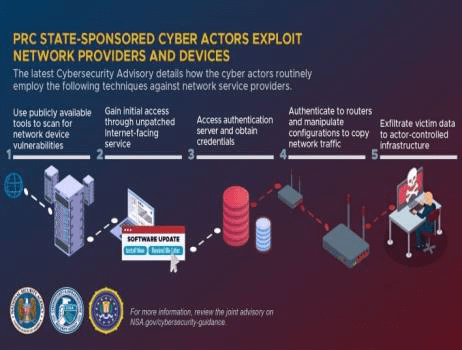
Xi Jinping came to power in 2012 and Chinese cyber-espionage became much more low-key. Intelligence restructuring occurred between 2016 and 2018 before official state sponsored hackers became operational aligned to the Belt and Road Initiative and the PLA military theaters. Coordinated attacks between military, civilian, and outside contractors have become more commonplace. Historically, Chinese cyberattacks were more widespread and now have become more stealthier with attribution becoming more difficult. Typical targets now have become more focused such as Covid vaccine information, election, telecom, Hong Kong, Tibet, Uyghur muslims. Exploiting third-party software has become more common and then targeting specific companies. Another key malware exploit is targeting vendors operating within China such as supply chains, law firms and maliciously expand them globally. Organizations that supply multiple governments and provide services to other companies are a strategic focus for Chinese cyber-espionage activities and need to maintain constant vigilance.
Espionage campaigns against global governments have become indelibly linked to strategic Chinese goals such as the Belt and Road Initiative. This has led to funding corruption and aligning local interests with China investments. Interference in elections to prop up Chinese sympathetic governments has been more involved in monitoring rather than influencing local elections. Advance notice of anti-China sentiment is used to feed into propaganda campaigns, social media disinformation and diplomatic attacks to further their political goals. A lot of countries that are reliant on investment and military support from China do not expose cyberattacks when they are clear about the motivations for such attacks.
Cyber crime such as crypto currency attacks and blackmail are frequent side effects of contracted hacker groups that try to make money in addition to their primary cyber-espionage targets. Conducting business in China also comes with certain risks as third party programs that are mandated for use in order to operate in the region. A majority of Chinese cyber-espionage is aimed at targeting it’s neighbours and testing it’s capabilities. Advanced AI capabilities to target Uyghur and Tibet internally are a common thread in frequent cyberattacks to build up capabilities in the region. The deployment of common toolkits across hacker groups such as APT10 (Bronze Riverside, Potassium, or Stone Panda), APT27 (Bronze Union, Emissary Panda, or Lucky Mouse), and APT41 (Barium, Bronze Atlas, or Wicked Panda) is a well known fact that strategic goals are being aligned and tasks issued by a central authority when it comes to cyberattacks from China. Over the past two decades, China has been at the forefront of violating the sovereignty of the largest number of countries in order to pursue an imaginary goal of confronting the West. Over just the past month, we have seen attacks on government targets in Vietnam, Thailand, and Indonesia as well as civilian hacking operations against Mongolia, Papua New Guinea, Ghana, Zimbabwe, and Nigeria. Targets in Asia and Europe have been known to receive fake emails with an EU Commission letter in order to facilitate hacking operations over the past few years. It is unclear as to how many people are engaged in this industry within China, but the scale and volume of operations suggests that hacking is fast become a career choice within China and the entire field has become industrialized.












